In the domain of network protection, understanding what is social engineering attack has become fundamental for the two people and associations. Social engineering attacks control human brain research to acquire unapproved admittance to frameworks, delicate data, or secure areas. As opposed to taking advantage of specialized weaknesses, these attacks focus on the human component, depending on trickery, trust, and mental control. As innovation develops, so do the strategies and refinement of social engineering attacks. In this article, we’ll investigate how man-made reasoning (artificial intelligence) is changing the scene of social engineering, making it more risky and unavoidable than any other time in recent memory.
What is Social Engineering Attack?
To comprehend the development of social engineering, responding to the inquiry: What is a social engineering attack is urgent first? A social engineering attack is any endeavor to maneuver individuals toward disclosing private data, giving access, or performing activities that compromise security. These attacks might include pantomime, trickery, or mental control. The objective is to take advantage of the human way of behaving to sidestep security conventions, instead of depending on specialized hacking procedures like taking advantage of programming weaknesses.
What is Social engineering?
What is social engineering attack?Social engineering is basically the craft of controlling individuals. It depends on the possibility that human way of behaving is the most vulnerable connection in the security chain. While online protection safeguards center around safeguarding organizations, frameworks, and applications, social engineering attacks frequently center around the people who associate with these frameworks. Assailants utilize different mental methods to acquire their objectives’ trust and mislead them into surrendering delicate data.
The Job of artificial intelligence in Friendly engineering attacks
As of late, the ascent of computerized reasoning (artificial intelligence) has decisively adjusted the scene of social engineering. While conventional social engineering depended on human association, the present artificial intelligence-controlled attacks have become more refined, mechanized, and adaptable. By utilizing computer-based intelligence innovations, for example, AI, normal language handling, and deepfake age, aggressors can complete huge scope crusades that are undeniably seriously persuading and harder to recognize.
One of the key procedures utilized in friendly engineering attacks is phishing, where aggressors mimic authentic elements to draw casualties into giving classified data. Man-made intelligence instruments are presently equipped for creating profoundly practical phishing messages, calls, and, surprisingly, counterfeit sites. These computer-based intelligence-produced tricks can be customized to individual targets utilizing openly accessible information from online entertainment and different stages, causing them to appear to be more trustworthy. This is a huge jump from the prior, more conventional phishing attacks that depended on mass messaging.
Another significant improvement is the utilization of deepfake innovation. Deepfakes use computer-based intelligence to make hyper-reasonable phony recordings or sound accounts that emulate the voice or presence of somebody the casualty trusts. For instance, an assailant could utilize deepfake innovation to imitate a Chief or supervisor and educate a representative to move cash or give login qualifications. In these cases, the casualty may not perceive the attack as a trick because the phony correspondence is unimaginably persuading.
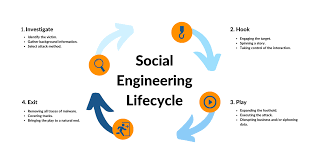
Social Engineering Attack Methods
Social engineering attack techniques. A few methods are regularly utilized in friendly engineering attacks. These include:
1. Phishing: Sending deceitful messages that seem to come from a confided-in source, like a bank or a partner, to fool casualties into uncovering delicate data.
2. Pretexting: Includes making a created situation to persuade the casualty to unveil private data. For instance, an aggressor could profess to be a client support specialist requesting account subtleties to “confirm” the casualty’s character.
3. Baiting: Offering something captivating, like free programming or admittance to restrictive substance, in return for individual data or activities that compromise security.
4. Quizzes and Surveys: Utilizing honest online tests to accumulate individual data that can later be utilized for additional modern attacks.
5. Vishing (Voice Phishing): Assailants use calls to mimic genuine substances, similar to a bank delegate, to separate private data.
What is the Best Control to Deal with Social engineering attacks?
The best control to deal with social engineering attack is a blend of mindfulness preparing and specialized measures. Instructing workers and people about the risks of social engineering and how to perceive dubious ways of behaving is significant. Associations ought to direct ordinary instructional courses, recreate attacks, and make a culture where representatives are urged to report potential security episodes.
On the specialized side, multifaceted confirmation (MFA) and powerful check frameworks can add an additional layer of insurance, making it harder for assailants to take advantage of human weaknesses. Simulated intelligence-based frameworks can likewise be sent to distinguish strange examples of correspondence, for example, messages from surprising IP addresses or unusual informing conduct.
Social Engineering Attack Model
An exemplary illustration of a social engineering attack includes a phishing email that seems to come from a bank, requesting that the casualty click a connection to “confirm” their record. The connection prompts a phony page that intently impersonates the bank’s genuine site. When the casualty enters their login subtleties, the aggressor catches the data and utilizations it to take assets from the casualty’s record.
What is Pretexting in Friendly Engineering?
Pretexting is a type of social engineering where the aggressor makes a bogus situation to get data from the person in question. For instance, an assailant could mimic an IT proficient requesting login qualifications to “fix” a specialized issue. Since the casualty believes the guise, they might give delicate subtleties that permit the assailant to acquire unapproved access.
Social engineering Counteraction
Forestalling social engineering attacks requires cautiousness, preparing, and a diverse security approach. Routinely teaching clients about the different strategies utilized by assailants is fundamental. Moreover, associations ought to carry areas of strength for out processes, use computer based intelligence driven security instruments, and screen network action for uncommon ways of behaving that might flag a social engineering endeavor.
Conclusion
The development of social engineering in the period of artificial intelligence denotes another time of online protection challenges. Aggressors currently approach amazing assets that computerize and improve their misleading strategies. Therefore, shielding against these attacks requires specialized shields, yet in addition a human-driven way to deal with security. Understanding what is social engineering attack and remaining refreshed on arising patterns is indispensable for safeguarding against these inexorably complex dangers.